Auto Disable a temp-use policy
BLUF:
Sometimes we need to allow access to some servers during a maintenance window.
Creating a schedule for such policies is a great idea, but sometimes you need a patch
thats out of schedule. I use this automation stitch to automatically disable outbound access
upon admin logout. If you're admin timeout short you might run into problems.
Auto-disable a policy upon logout
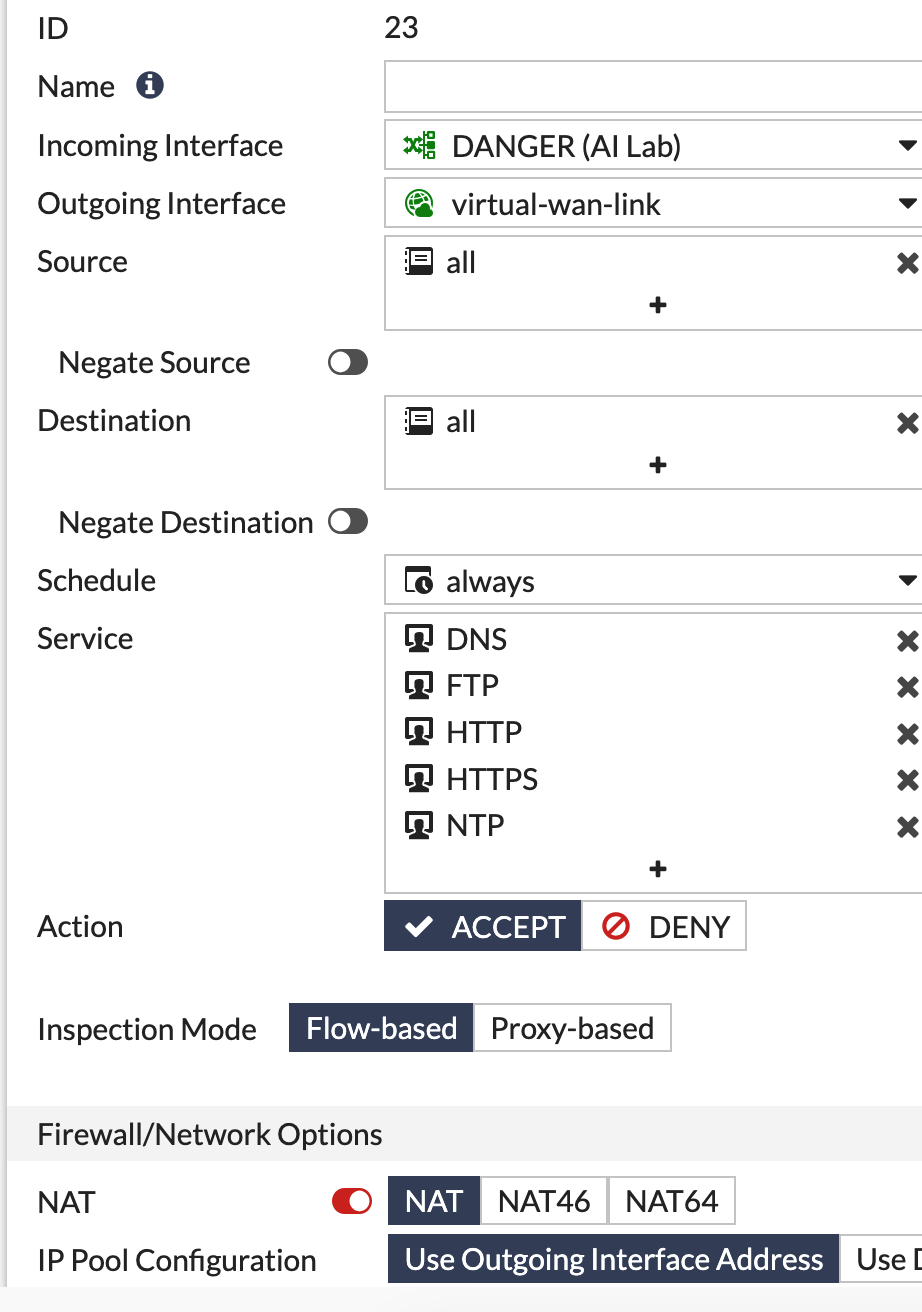
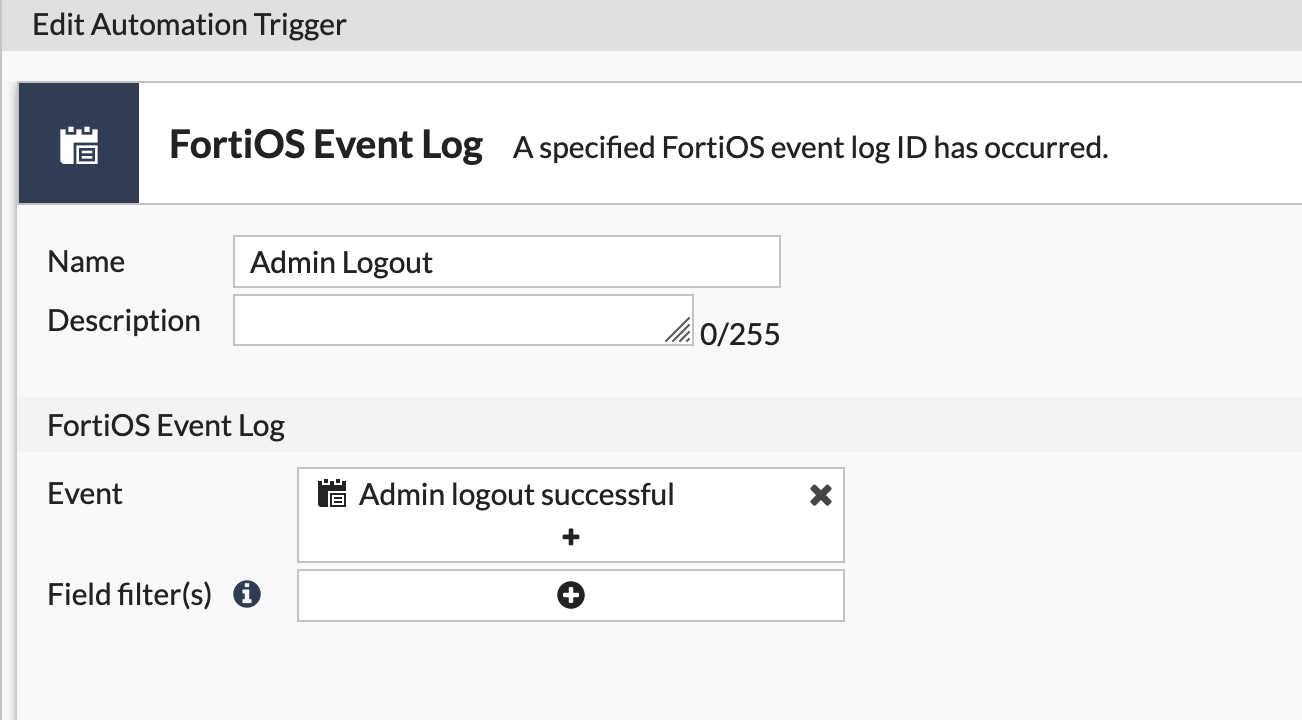
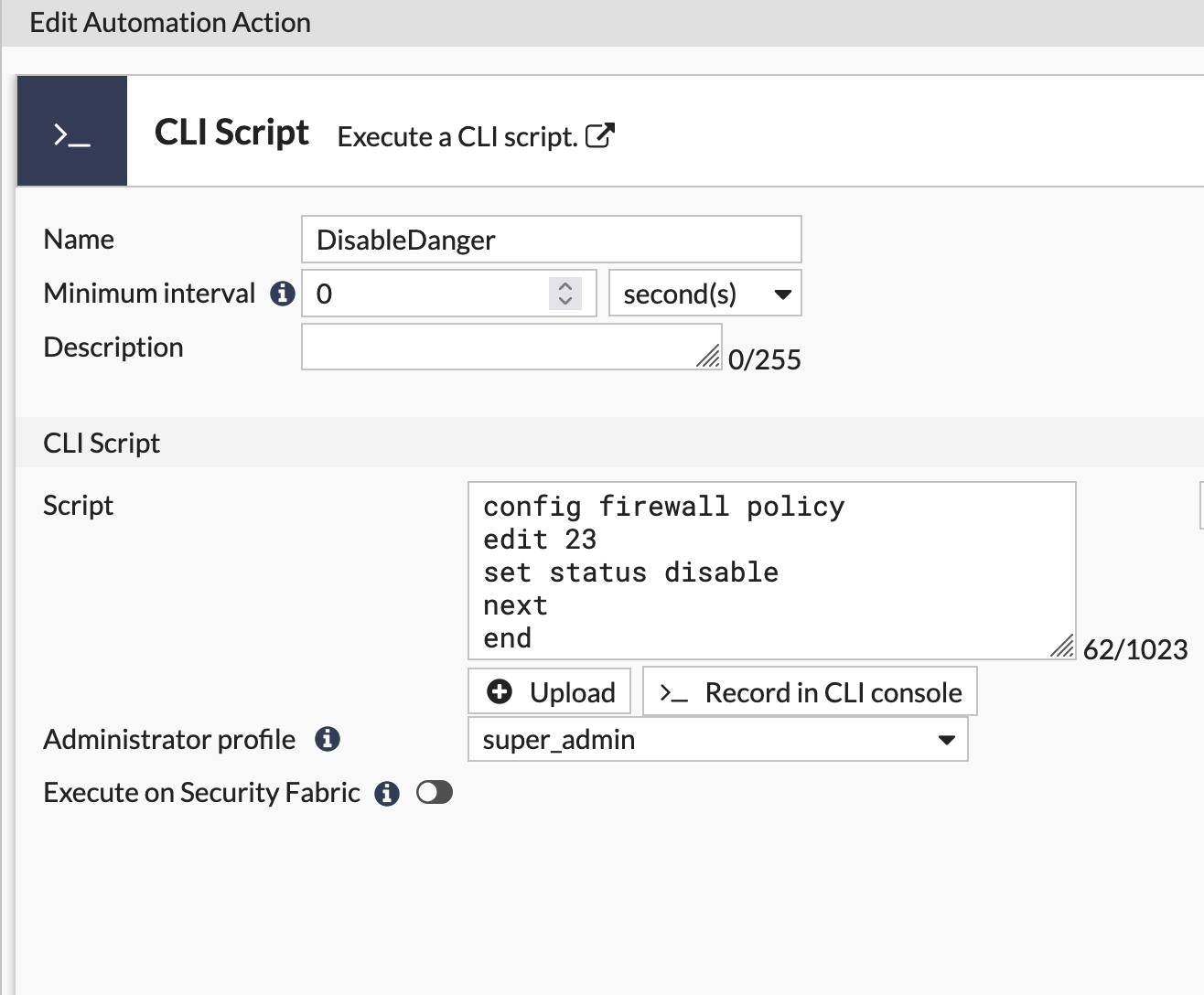
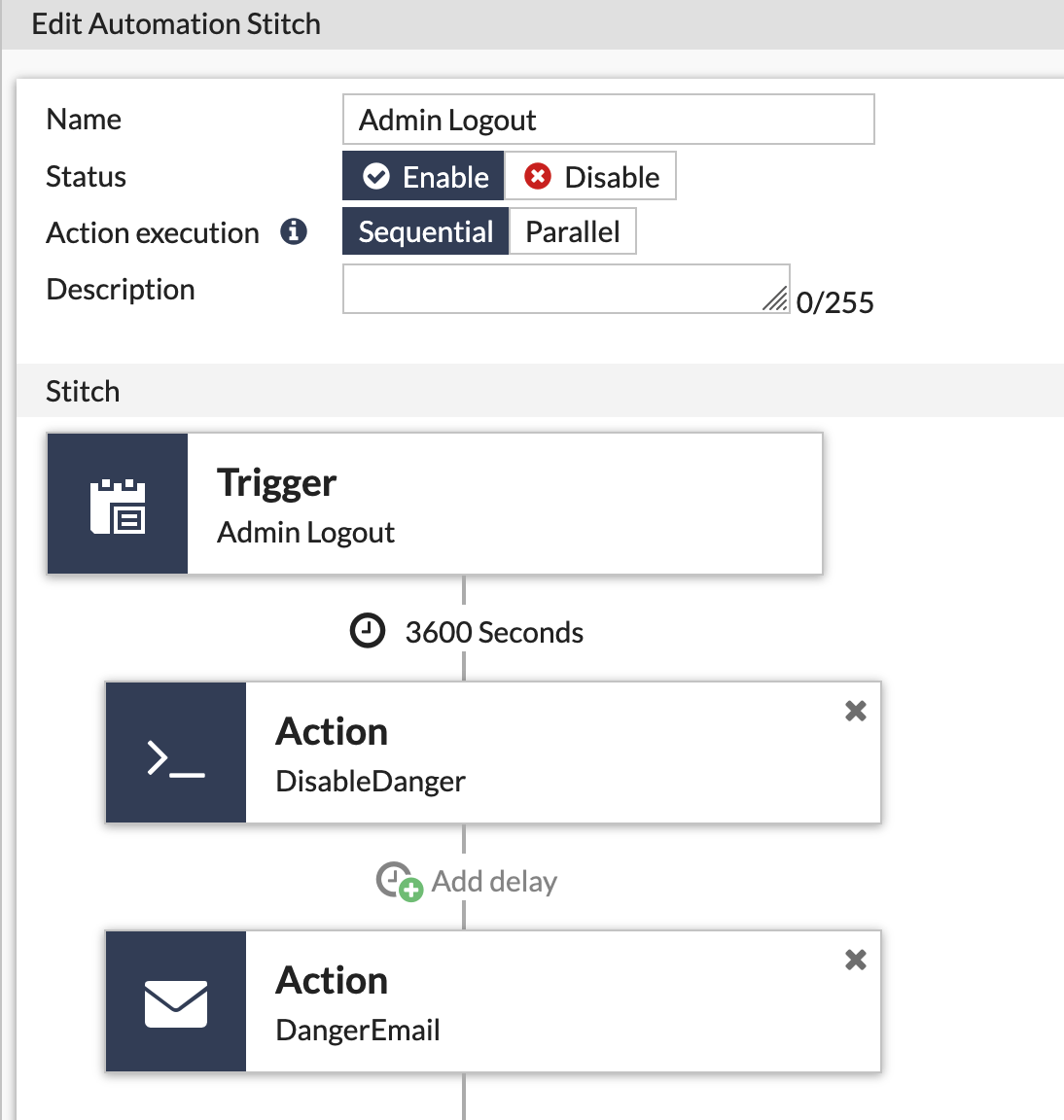
Servers in the DANGER network are not allowed access to the internet. Occaisionally, the servers in this segment require updates. This automation stitch serves to disable the outbound policy for this segment 5 minutes after the admin logs out.
Admittedly, this howto is light on explanation. As time allows, I'll update it. But you should have no problem implementing this Automation stitch.
💡 This is a convenience feature for environments where strict maintenance windows are not used. This is not a replacement for proper policy. Its simply a way to avoid leaving the barnyard gate open.
Create an outbound policy
Create a Trigger
Create an Action
Assemble the automation stitch
Usage
Upon login of the firewall, simply enable the policy that allows outbound internet connectivity. Then, go about the process of performing upgrades.
💡 Don't forget: Your admin session will time-out due to inactivity. If your timeout is set to 5 minutes, and you've added a 5 minute delay to the automation stitch, you'll have 10 minutes to perform your work. You can always extend the first five minutes by navitating to a new page in the fortigate.