Event Handlers & Automation Stitches
BLUF:
Fortinets' Security Fabric can do some our work for us.
FortiAnalyzer Even Handlers can perform an action when specific logs are seen.
Fortigate Automation Stitch can perform some action when some trigger happens.
Combining the two results in less worklaod for the operator.
Event Handlers & Automation Stitches
Actionable Intelligence from FortiAnalyzer can be used to trigger an action on a FortiGate.
Configuring an Event Handler
Its always easier to clone and object than it is to create one from scratch. I found an Event Handler called IPS - High Security and cloned it
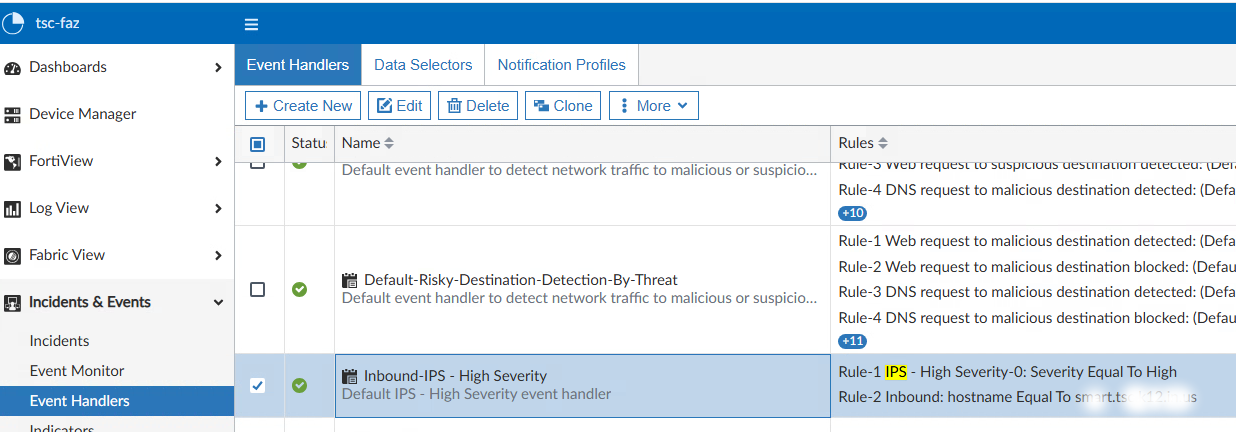
As you can see, it has two Rules (right column) instead of one. This was a mistake on my part. In the next screenshot, I've expanded each rule so they're visible, but please note that these rules are incorrect. Later in this document I will show a correction. Please view the documentaion for Event Handlers for finer control.
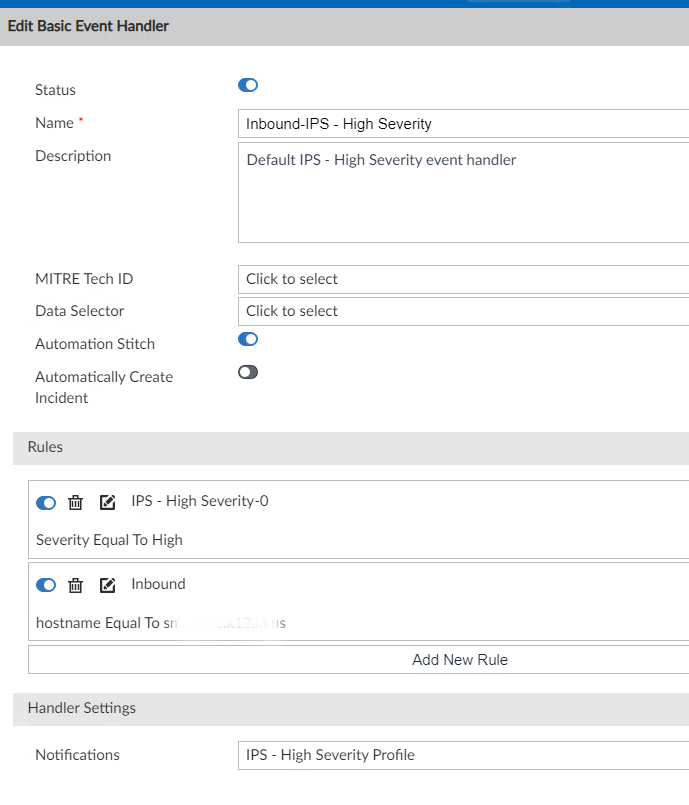
💡Ensure you switch Automation Stitch to on if this Event Handler will be used to perform some action on the FortiGate Firewall.
Configuring the automation stitch
Lets define an automation stitch that quarantines the offending IP automagically
⚠️ You must define a Trigger and an Action before you can create an automation stitch. Triggers define logical nouns while Actions describe logical verbs.
Defining a trigger
Under Security Fabric, click on Automation, click on Trigger (at the top of the page), and click Create New.
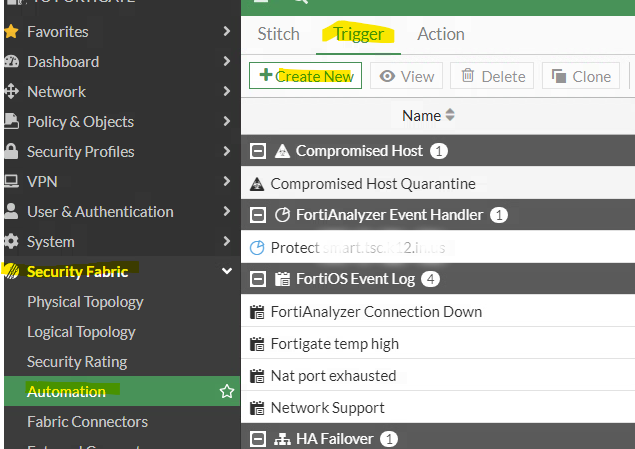
Select FortiAnalyzer Even Handler and configure the trigger to use the Event Hander we created earlier.
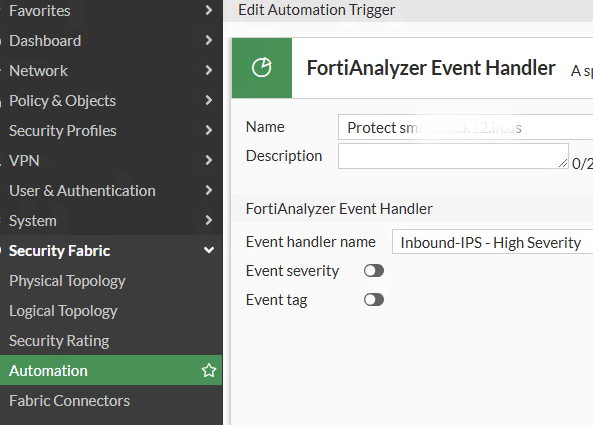
Defining an Action
Under Security Fabric, click on Automation, click on Action (at the top of the page), and click Create New.
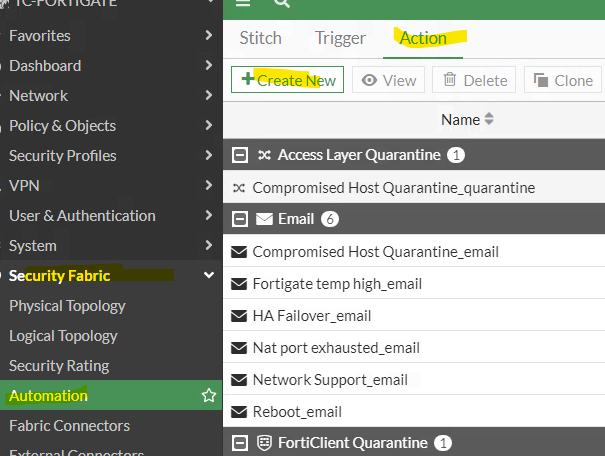
Select IP Ban and name the Action.
Assemble the Automation Stitch
Under Security Fabric, click on Automation, click on Create New. Then select your Trigger and Action.
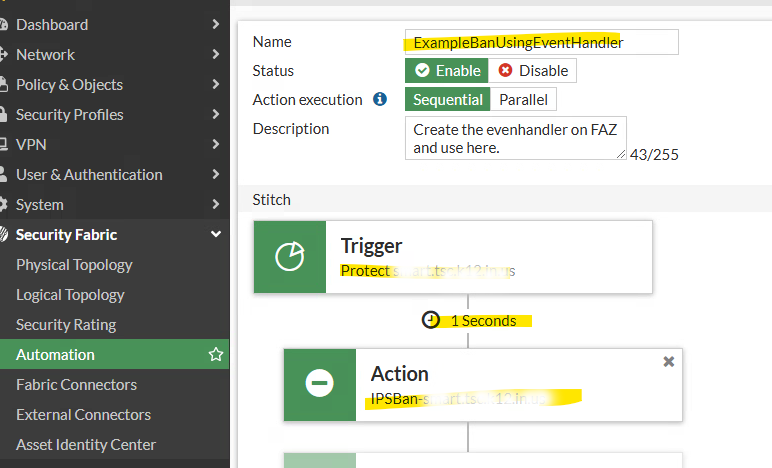
Note: I added an optional 1 second delay to demontrate the capability. It is not necessary in most cases.
Observe the Event Handler & Automation Stitch
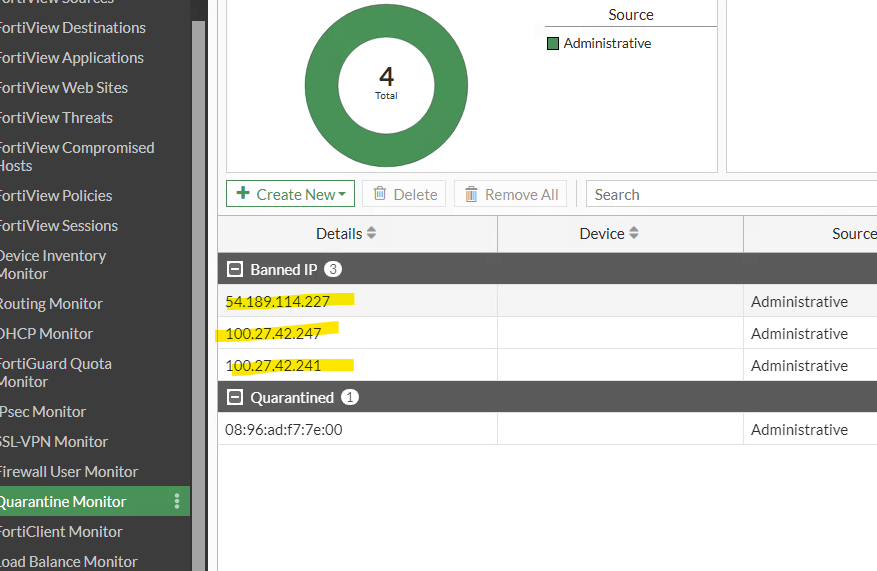
Use the Quarantine Monitor in the Dashboard to view the list of Banned IP's.
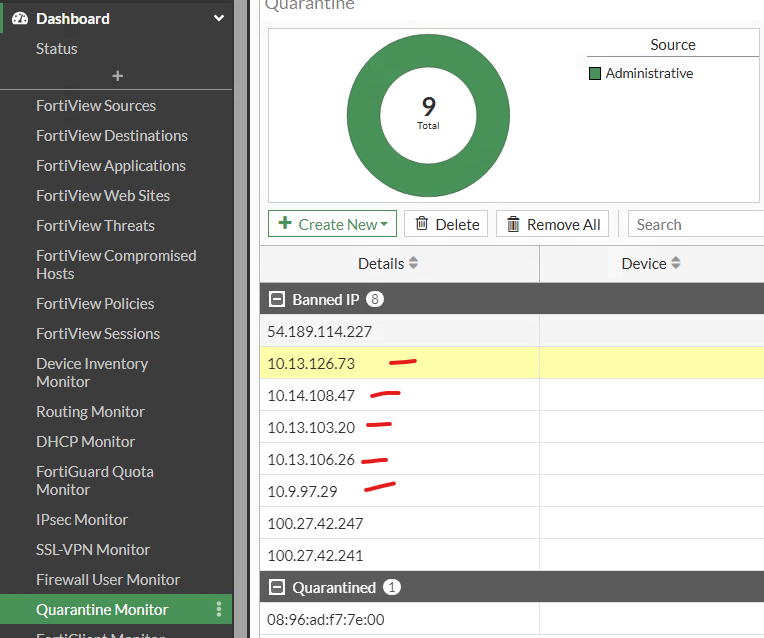
Several internal hosts have been quarantined. Some investigation is required. In this case, I'll ignore src addresses from 10.0.0.0/8 in the event handler.
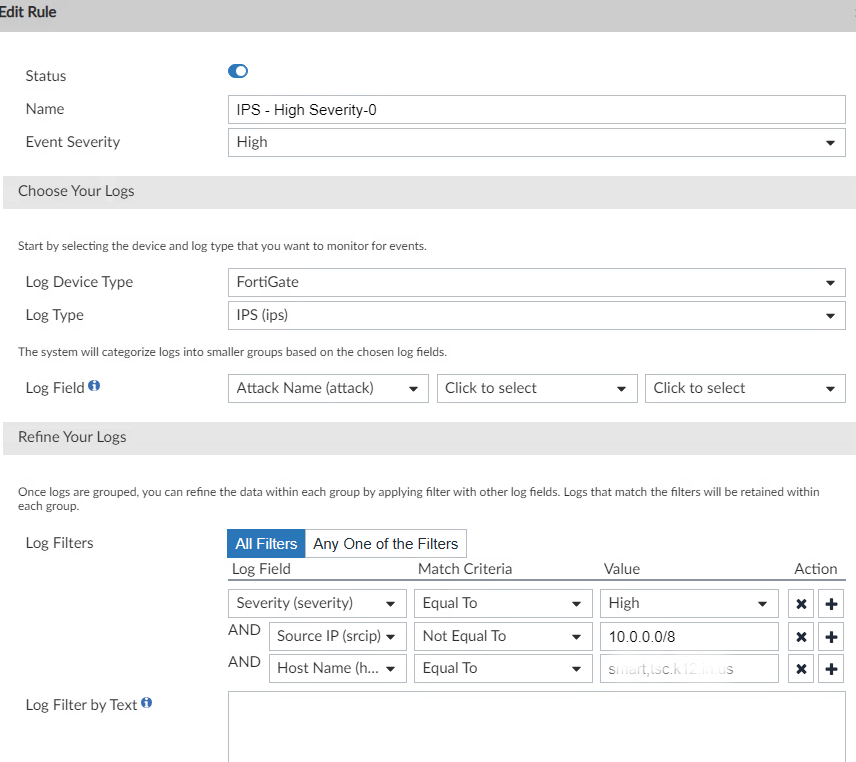
This modification should behave in such a way that only outside attackes are blocked.
☠️ Please note, I made a mistake when first defining the Event Hander. There were two rules when there should have been one with multiple AND operators. I fixed the mistake when I added the 10.0.0.0/8 src-addr rule. I hope you spoted it.
The quarantine list is looking much better after modifying the Even Handler.